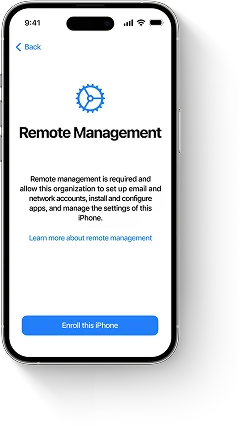
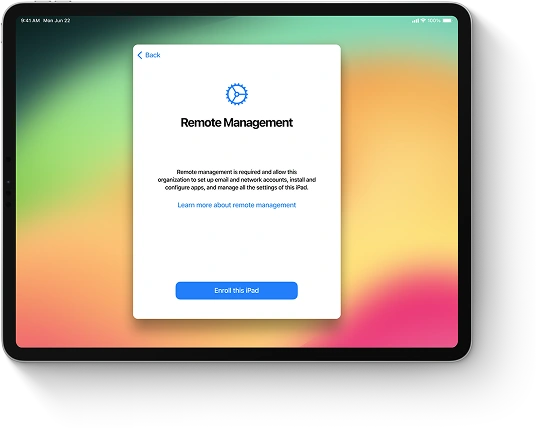
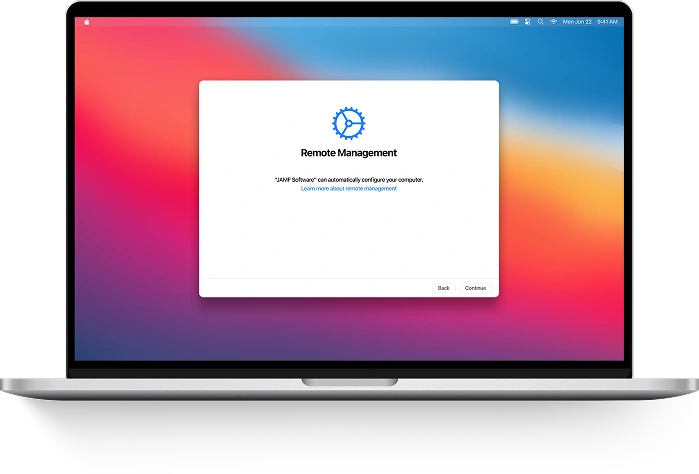
Since MDM software is based on client-server architecture, MDM server is an essential part of it. MDM server pushes notifications, configurations, apps, and policies managing clients which are all mobile devices enrolled in MDM program (iPhones, iPads, iPods touch and MacBooks). This process is done using over-the-air, or OTA, technology which allows IT administrators to remotely manage a large number of devices without a need to physically have them at their fingertips. This way, they can install, remove or inspect profiles, remove passcodes, install and uninstall apps, monitor and track enrolled devices, as well as lock or erase those misplaced or lost.
This is how Apple describes work of MDM protocol and MDM server:
“The MDM protocol is built on top of HTTP, transport layer security (TLS), and push notifications. The related MDM check-in protocol provides a way to delegate the initial registration process to a separate server. MDM uses the Apple Push Notification Service (APNS) to deliver a “wake up” message to a managed device. The device then connects to a predetermined web service to retrieve commands and return results.”
The main point of this description is that HTTPS server deployment is a must for Mobile Device Management implementation. This way, the mentioned HTTPS server becomes the MDM server. But it doesn’t push commands to managed devices directly and can’t manage them without distribution of MDM payload containing profiles to each device enrolled.
To give you a clear picture of the process, here is what happens every time when client devices interact with MDM server:
1. Server makes a request for push notification using Apple Push Notification Service (APNS).
2. Apple pushes the notification directly to the device.
3. The device connects to the MDM server with a request for commands and executes them. The client responds to the MDM server with the result.