MDM, or Mobile Device Management, software works based on client-server architecture. This means the MDM process involves a client and a server. In MDM case, mobile devices act as clients and, obviously, MDM server acts a server. MDM works not only with smartphones or tablets, it can also manage laptops. Currently, the number of mobile devices involved in business activities is huge and continues to grow involving corporate-owned devices, as well as personal devices which employees use for work purposes. The reason why MDM became an essential part of daily routine is that all these devices must be properly managed and supervised with minimum physical involvement of employees, both end-users and IT departments.
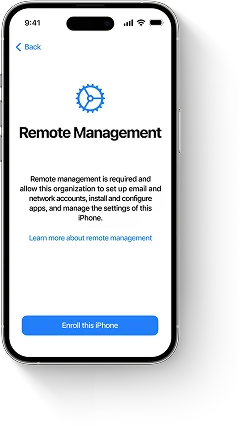
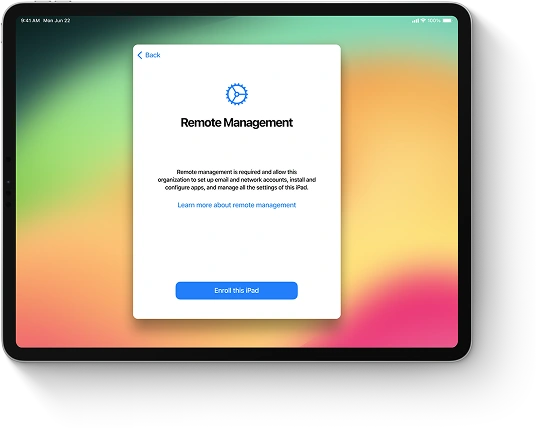
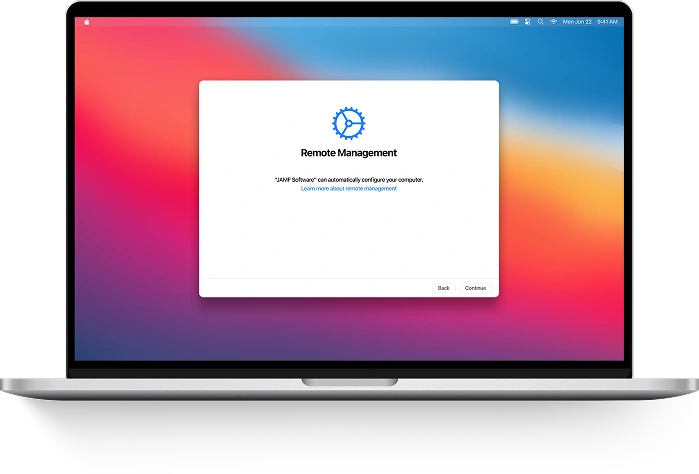
Before an MDM server can configure devices and push settings, security policies and any restrictions related to apps, accounts and internet usage, MDM payload with configuration profile must be deployed in device’s settings. Once a device is enrolled in an MDM program, MDM server starts pushing settings, updates and so on to it using over-the-air, or OTA, technology.
Basically, MDM work comes to four steps as MDM server can’t push notification directly to end-points, which are managed mobile devices:
1. MDM server uses Apple Push Notification Service (APNS) to request a “wakeup” notification pushing to mobile devices.
2. APNS pushes these notifications to devices letting them know they need to connect with the MDM server for commands.
3. Mobile devices connect to the MDM server requesting commands and actually execute them.
4. Managed mobile devices respond to the MDM server with the result. This way, IT departments or administrators do not need to manually configure devices enrolled in MDM program. This approach is especially beneficial for businesses dealing with a large number of devices in different locations as they make sure that every single device having access to corporate data is properly managed ensuring data security and proper usage of devices involved in business activities. This kind of remote management also allows to remotely track, lock and erase devices considered lost or stolen preventing sensitive data leakage.